One of the most common causes for AS2 connection errors is not having the correct certificates configured for your trading partner within Arc. In an AS2 connection, your partner’s SSL server certificate is validated against your system’s security settings to proceed with an SSL handshake, and their S/MIME certificate is used for the validation of signed messages and encryption of outgoing messages.
Ordinarily, these certificates are exchanged as part of the setup of a new AS2 connection, but certificates are commonly replaced, and you may be left with a connection that is not working after an update from your partner. The following methods are not foolproof, but there are possible methods for obtaining these certificates without direct contact from your partner.
Obtaining the SSL Server certificate
This is straightforward - place your partner’s receiving URL in a browser:
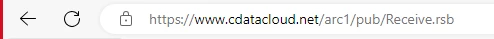
If the URL resolves, click on the lock icon and locate the server certificate.
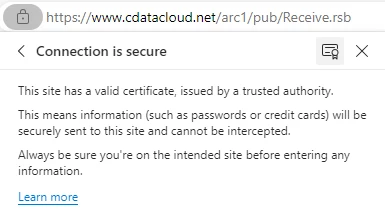
the certificate viewer will give you an opportunity export the certificate - for the purposes configuring the SSL certificate in Arc, you will want to export the leaf certificate (the end of the chain):
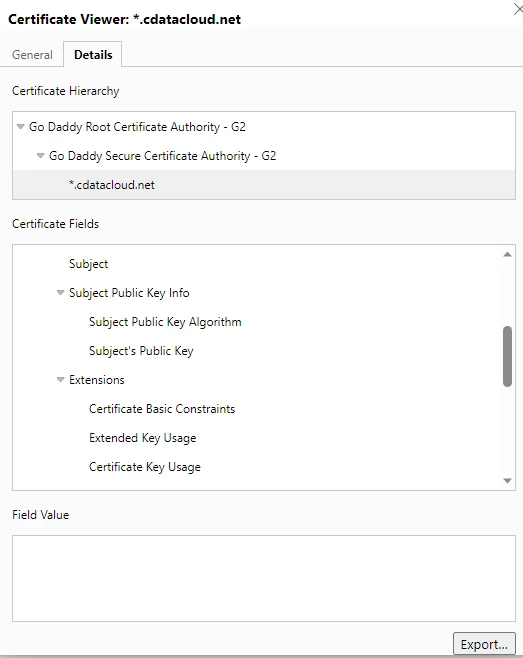
Once exported, you can configure this certificate in the Trading Partner Certificates->TLS Server Certificate field.
Extracting your partner’s public key from an MDN log
If your trading partner replaces their certificate with one that is not configured in your connection to them, you may encounter an error like this when sending to them:
The receipt signature could not be verified: The certificate was not found in the specified store.
This is an indication that the certificate used to sign the MDN receipt is not a match for the certificate configured for the partner. What you may not know if that many times, the certificate is embedded in the signature returned in the MDN returned.
From the Logs selection in the administration console, it is possible to download the .mdn log for the transmission, which contains the MDN response.
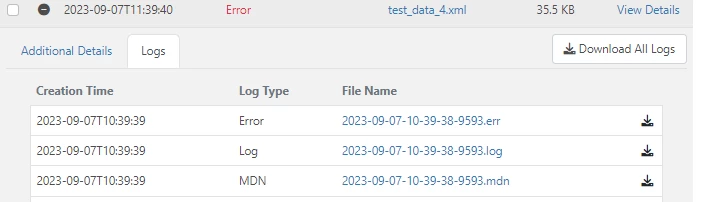
Attached to this thread is a utility built using the underlying security provider used by Arc, “WhoSignedThis”. Extract the contents of this zip into a folder on disk, and drop in a copy of the MDN in the folder:
If the MDN response contains a signed MDN that includes the embedded certificate, running WhoSignedThis.exe will extract the certificate embedded in the signature into the directory, naming the new certificate with the AS2 Identifier of the party signing the message:
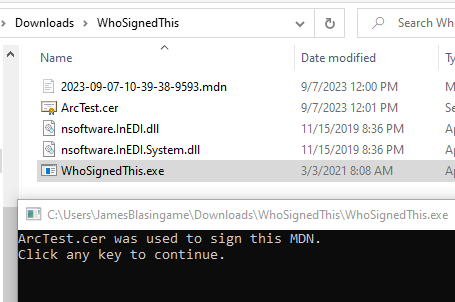
This only works if the trading partner returns a signature that contains the certificate, but if so, it can be a quick way to find out their new certificate before contacting them


