Overview
Bearer token authentication can be one of the more finicky authentication mechanisms to implement within Arc. The reason is because the token lifetime is very short and automatic token refresh isn’t something that is built into that mechanism, like it is with OAuth 2.0. Thus, a new token needs to be generated and manually re-entered every time the old one expires. This isn’t really practical in Arc since many flows rely on automation to continually process files or make requests to APIs. Luckily, in Arc t is possible to create a custom script that gets a new token for each request that you send and then the token is dynamically evaluated within the REST connector.
The Script
The script that should be used here is going to need to be responsible for two things:
1) Obtaining a refresh token from the token endpoint of your API
2) Adding the token as a header onto the message within Arc
This will fire every time your input file passes through the script and will get a new token for each file you have to send the REST connector. This is actually the intended way that bearer token authentication should be used, since the lifetime of the tokens is so short. Fortunately, we have already written a script that does this and it is embedded within the script connector itself, within the "Snippets" dropdown:
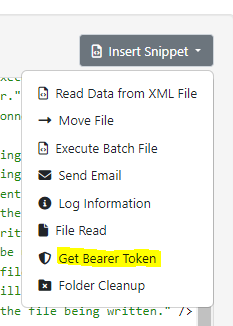
Selecting this option will give you a template script that looks like this:
<!-- This example expects the following inputs to be modified:
- http.URL: The URL of the resource to POST to in order to obtain the token.
- http.postdata: The data that should be POSTed to the given URL. Often this is
is a username and password in json format.
- json.map:token: The jsonpath where the token will be returned in the response.
Once the token is obtained, it is added as a "token" header to the output message.
The output message data is the same as the input data. -->
<arc:set attr="http.URL" value="http://myspecialurl/api/token" />
<arc:set attr="http.postdata" value='{"password":"1234","username":"test"}' />
<arc:call op="httpPost" in="http" out="response">
<!-- Pass in the json response that contains the token to jsonOpen. -->
<arc:set attr="token.text" value="[http:content]" />
<arc:call op="jsonOpen" in="token" out="handle">
<!-- Call jsonDOMGet with the handle that was obtained from jsonOpen. -->
<arc:set attr="json.handle" value="[handle.handle]" />
<arc:set attr="json.map:token" value="/json/access_token" />
<arc:call op="jsonDOMGet" in="json" out="result" >
<!-- Set the token as a "token" header on the output message. -->
<arc:set attr="output.header:token" value="[result.token]" />
</arc:call>
</arc:call>
</arc:call>
<!-- Push out the original input file. -->
<arc:set attr="output.filepath" value="[filepath]" />
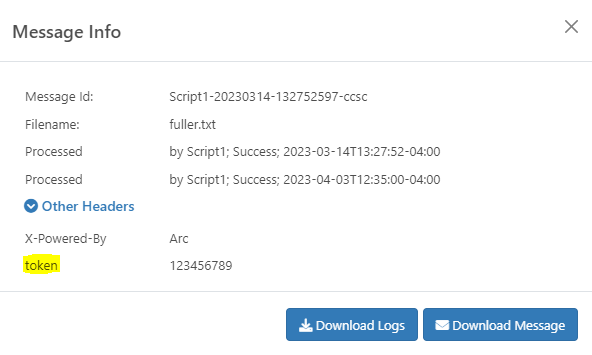
<arc:push item="output" />The script provides simple instructions on how to adopt it to your specific use case. Once configured correctly, you should see a “token” header on the output file with the value set to the token received from your token endpoint:
The REST Connector
Then, once you have the script working, generating a token and adding it as a header, you will need to make a few minor adjustments to the REST connector so that it works with getting the token from the header.
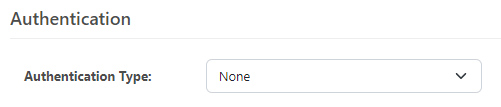
1) Set authenticate type to "none". The authorization will instead be built dynamically via an HTTP header and the token attached to the message header.
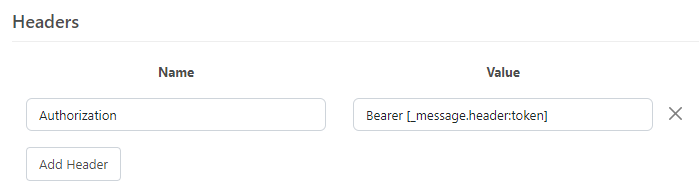
2) Create a custom header with a name of Authorization and a value of Bearer [_message.header:token] where the value of the message header is going to be the token value that was acquired in the scripted step before. This is actually how the Bearer Token authorization header is formed on the request (https://learning.postman.com/docs/sending-requests/authorization/#bearer-token)
3) Enable "Allow ArcScript in Headers" within the Advanced tab
If done correctly, you should now be able have input files flow into your REST connector with a “token” header on the Arc message, and that value will be evaluated within the HTTP request header of the REST connector. You should no longer need to manually get a token every time the old one expires.



